Zip and Unzip via SSH: Everything You Need to Know Compressing and extracting files is not only common on desktop computers. You may need to do the same things on your VPS. Zipping and unzipping files make it easy for you to download and move data around. To perform these actions, you need to run …
Category : AWS
16 posts
Sometimes you would need to extract or create an archive file, i.e to install a script, you would usually download an archive and extract it to continue the installation. The very first step in the process would be to identify the exact archive type by looking at the file extension. The most common archive types …
Introduction to S3 and EC2 file copy In this article, we are going to see how to copy files from ec2 instance to S3 bucket and vice versa, with the help of IAM roles and without having to use the AWS access key and secrets in the server. In AWS technical terms. Copying files from …
What is SSH SSH, or Secure Shell, is a remote administration protocol that allows users to control and modify their remote servers over the Internet. The service was created as a secure replacement for the unencrypted Telnet and uses cryptographic techniques to ensure that all communication to and from the remote server happens in an …
SSH, the Secure Shell, is a popular, powerful, software-based approach to network security.[2] Whenever data is sent by a computer to the network, SSH automatically encrypts (scrambles) it. Then, when the data reaches its intended recipient, SSH automatically decrypts (unscrambles) it. The result is transparent encryption: users can work normally, unaware that their communications are safely encrypted on …
Amazon’s Virtual Private Cloud (VPC) is a foundational AWS service in both the Compute and Network AWS categories. Being foundational means that other AWS services, such as Elastic Compute Cloud (EC2), cannot be accessed without an underlying VPC network. Amazon VPC and Subnets Amazon VPC enables you to connect your on-premises resources to AWS infrastructure …
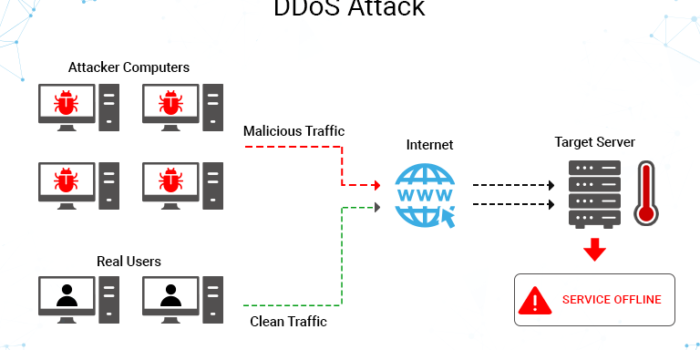
A Distributed Denial of Service (DDoS) attack is a non-intrusive internet attack made to take down the targeted website or slow it down by flooding the network, server or application with fake traffic. When against a vulnerable resource-intensive endpoint, even a tiny amount of traffic is enough for the attack to succeed. Distributed Denial of …
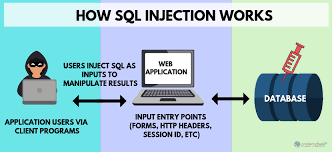
What is An SQL Injection Vulnerability? Within this blog post we are trying to shed a light on the technical aspects of SQL injections and what you can do to effectively avoid them. Non-Technical Explanation of the SQL Injection Vulnerability Imagine a fully-automated bus that functions based on instructions given by humans through a standard …
How To Setup Cron Jobs In Magento 2 Via SSH And Cpanel Clearly, from the viewpoint of management, the importance of automatic running the routine maintenance jobs in the background is undeniable. Since then, Linux Cron utility is an effective way to schedule a routine background job at a specific time and/or day on an on-going …
Introduction Amazon Web Services (AWS) has an extremely wide variety of services which cover almost all our infrastructure requirements. Among the given services, there is AWS Systems Manager which is a collection of services to manage AWS instances, hybrid environment, resources, and virtual machines by providing a common UI interface for all of them. Services …